WTF is Defense in Depth?
Find a definition and several examples below. Is defense in depth still relevant in 2023?
The TL;DR Summary
- Defense in depth is a multi-layered cybersecurity strategy that protects critical assets by combining preventive, detective, and reactive measures.
- Redundancy is key: at least two or more controls must fail before a system is compromised
- Examples of defense in depth include server security, endpoint security, and web application security.
- Defense in depth remains relevant in 2023 due to the complexity of modern cyber threats, compliance requirements, and the human factor in cybersecurity.
What is Defense in Depth?
Defense in depth is a cybersecurity strategy that employs multiple layers of independent protection to guard against potential threats, ensuring that at least two or more controls must fail before a system is compromised. It's like having multiple locks on your door— if one lock gets picked, the others are still there to keep intruders out!
Key Concepts
As security engineers, our primary goal is to keep our systems and data safe from potential threats. One of the most effective strategies to achieve this is using the principle of defense in depth. In its essence, defense in depth involves implementing multiple layers of security measures to protect an organization's critical assets. This approach ensures that even if one mechanism fails, others are in place to halt or mitigate the attack.
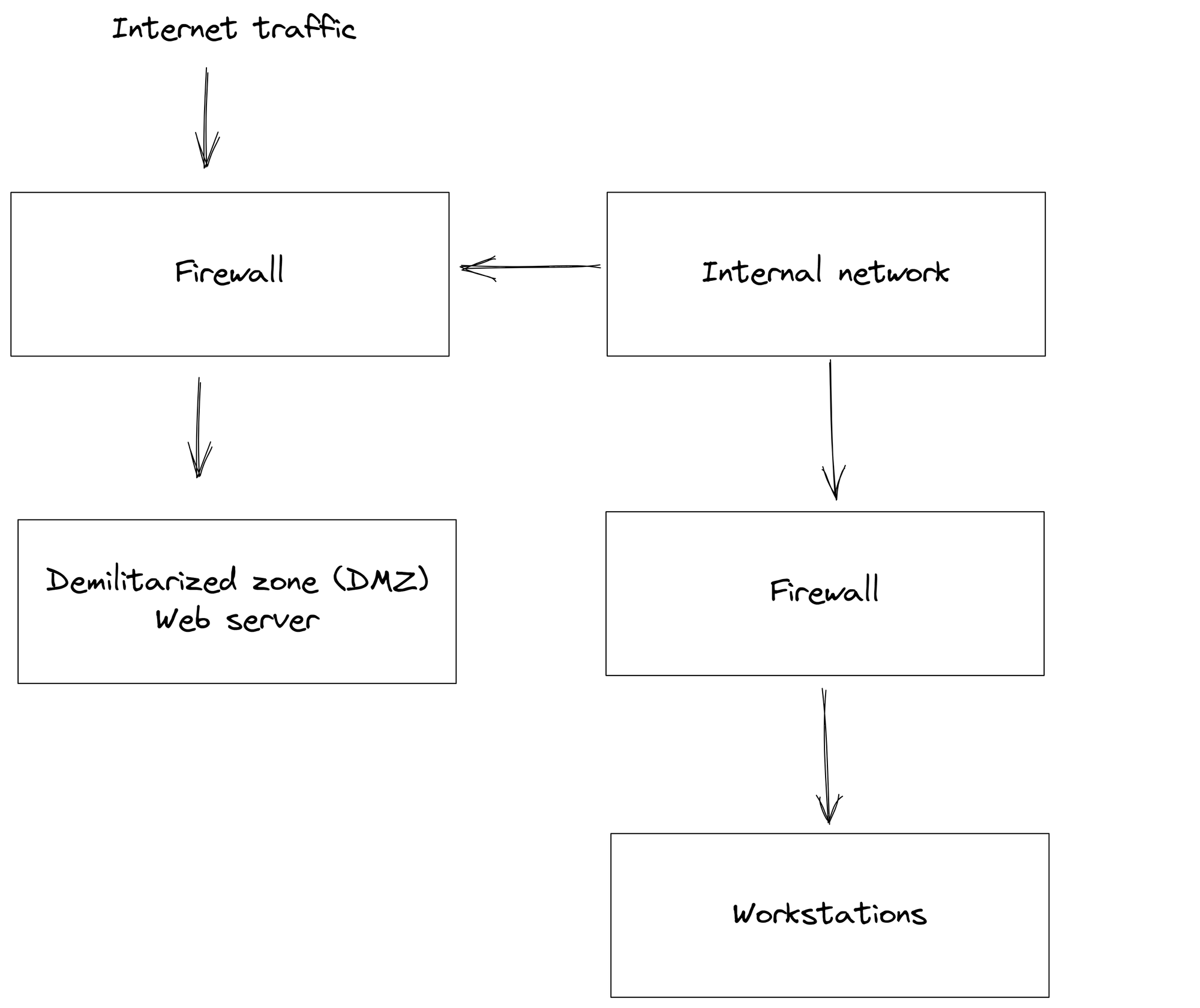
The concept of defense in depth originated from military strategies, where various obstacles or hurdles are placed to delay or deter an enemy's advances. In the context of cybersecurity, these obstacles are represented by a combination of technical, physical, and administrative controls. An effective defense in depth strategy consists of preventive, detective, and reactive measures that work in synergy. Preventive measures include firewalls and antivirus software, while detective mechanisms focus on intrusion detection systems and log monitoring. In case an attack is successful, a comprehensive incident response plan as a reactive measure enables swift action to limit the damage.
When implementing defense in depth, it's crucial to identify critical assets and prioritize security efforts accordingly. Understanding potential threats helps to design tailor-made layers of security for the particular environment. One of the primary tenets of defense in depth is ensuring that no single point of failure exists. This redundancy adds resilience to the security infrastructure and promotes a proactive approach to cybersecurity, anticipating threats before they can materialize.
By employing a multi-layered approach with a mix of preventive, detective, and reactive controls, organizations can minimize their exposure to risks and create a resilient cybersecurity posture against potential threats.
Examples of Defense in Depth
This might be getting a bit abstract. Let's look at what it might look like in practice through three examples:
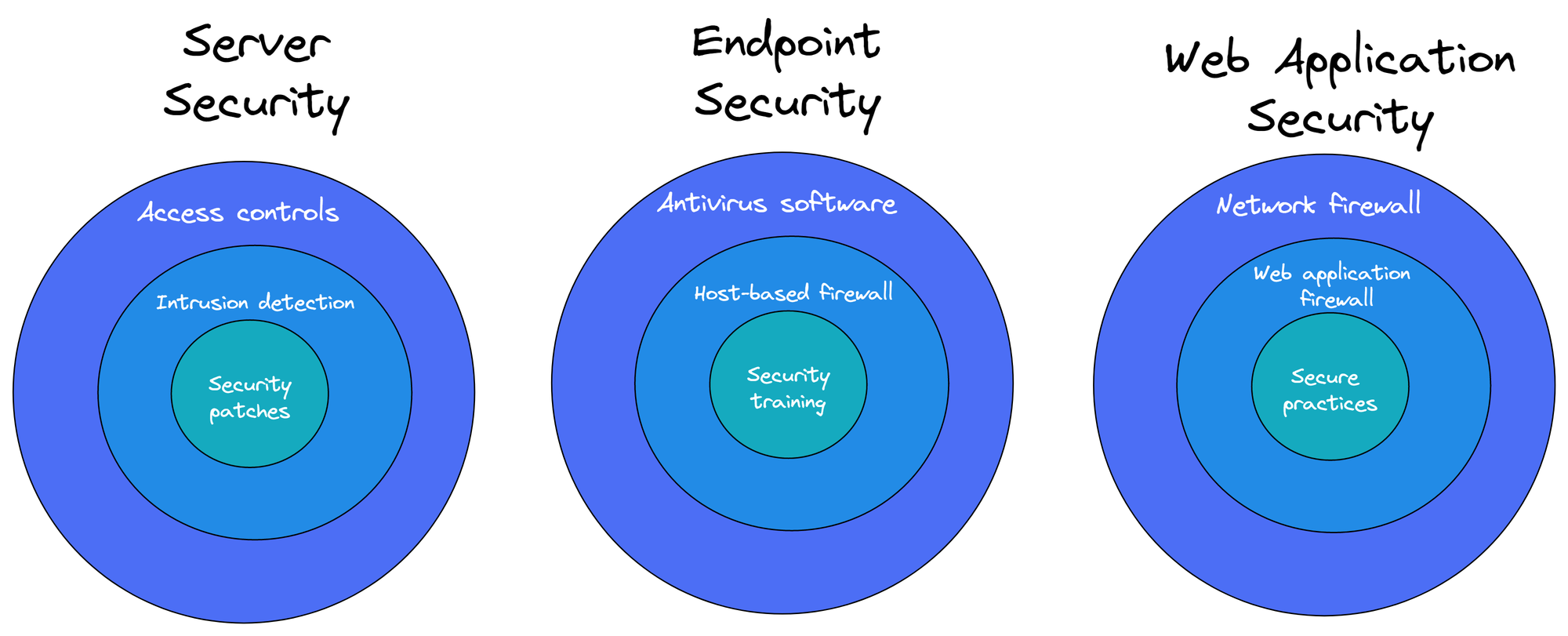
Example 1: Server Security
A server might be protected by multiple layers of security, which include:
Access Controls: Implementing access control measures, such as user authentication and authorization, means that only authorized individuals can access sensitive data or resources. This helps prevent unauthorized access and potential data breaches.
Intrusion Detection System (IDS): An IDS monitors network traffic or system activities, detecting and alerting on suspicious behavior or potential threats. This enables a quick response to mitigate any potential damage from intrusions or malicious activities.
Security Patches: Regularly updating the operating system and software with the latest security patches helps protect the server from newly discovered vulnerabilities. Timely patching reduces the risk of exploitation by cybercriminals and keeps the system up-to-date with the latest security measures.
Example 2: Endpoint Security
In a corporate network, a user device (such as a laptop or desktop computer) is protected by:
Antivirus/Antimalware Software: This layer provides real-time scanning and detection of viruses, malware, and other potentially harmful software. It helps prevent infection and keep the device secure and operational.
Host-based Firewall: A host-based firewall is a software firewall installed directly on the user's device. It provides an additional layer of protection by monitoring and controlling incoming and outgoing network traffic based on predetermined security rules.
Security Awareness Training: Providing users with security awareness training helps them understand the potential risks and best practices associated with handling sensitive data and using digital devices. This knowledge enables users to recognize threats, such as phishing emails or social engineering attacks, and respond appropriately to minimize the risk of security breaches.
Example 3: Web Application Security
In the context of a web application, a defense in depth approach could include the following layers of security:
Network Firewall: This outermost layer filters incoming and outgoing traffic, only allowing specific types of connections based on predefined rules. It helps block unauthorized access and protect the network from potential threats.
Web Application Firewall (WAF): The WAF operates at the application layer, monitoring and filtering HTTP/HTTPS traffic. It identifies and blocks malicious requests, such as SQL injection or cross-site scripting (XSS) attacks, to protect the web application from exploitation.
Secure Web Application Practices: This layer includes secure coding practices, input validation, output encoding, and proper session management, which help minimize vulnerabilities and strengthen the web application against attacks.
Why Defense in Depth is Still Relevant in 2023
As we continue to face a myriad of cyber threats in 2023, it's essential to reassess the relevance of defense in depth as a cybersecurity strategy. While the landscape and threat vectors have evolved significantly, the core principles of defense in depth still hold their value.
The increase in complexity and sophistication of cyber threats underscores the need for a multi-faceted approach. A single layer of security is insufficient to combat modern threats. The multi-layered design of defense in depth allows organizations to maintain a strong security posture, even when faced with new attack techniques.
Regulatory and Compliance Requirements: Many regulatory frameworks and compliance standards, like GDPR, PCI DSS, and HIPAA, emphasize the importance of layered security controls. Implementing defense in depth aligns with these requirements, ensuring that businesses stay compliant and avoid potential fines.
The Human Factor: Defense in depth considers the human factor in cybersecurity, recognizing that users can be both the strongest and weakest link in the security chain. Measures such as security awareness training and education against social engineering, which are part of a defense in depth strategy, are more relevant than ever.
Have we got anything wrong? We'd love to hear your corrections. Drop us a line anonymously here, or sign up let us have it in the comments below.