The Top 7 Security Engineering Stories From the Past Week
Enjoy our weekly curated roundup, and have a great weekend!
Stuff we found elsewhere
Why is OAuth still hard in 2023? | Nango Blog
We implemented OAuth for the 50 most popular APIs. TL;DR: It is still a mess.

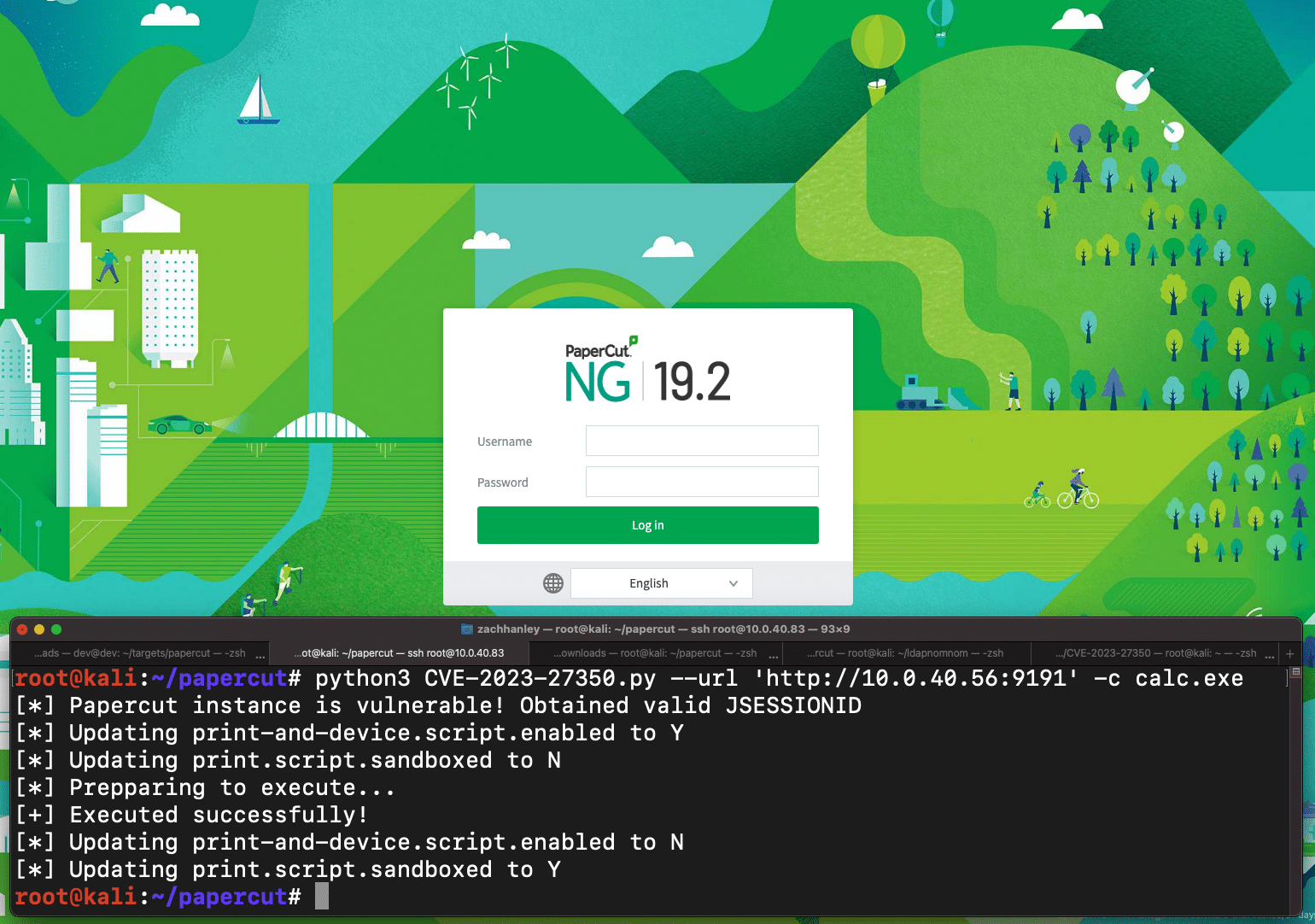
PaperCut CVE-2023-27350 Deep Dive and Indicators of Compromise
PaperCut CVE-2023-27350 Technical Deep-Dive, Indicators of Compromise, and Exploit Proof-of-Concept.
Google Authenticator now supports Google Account synchronization
Christiaan Brand, Group Product Manager We are excited to announce an update to Google Authenticator , across both iOS and Android, which a…

GitHub - memorysafety/sudo-rs: A memory safe implementation of sudo and su.
A memory safe implementation of sudo and su. Contribute to memorysafety/sudo-rs development by creating an account on GitHub.
Stuff we wrote
WTF is DevSecOps?
Buzzword or shift-left revelation? We dive into the intriguing new world of DevSecOps.

Preventing SQL Injection: Is WAF Enough?
Probably not TBH

The Beginner’s Guide to Honeytokens (AKA Canary Tokens)
Get a high-level overview of honeytokens in cybersecurity, with examples.




